Game of Pwners CTF 2017 - SIGINT 100 - Answer
While traversing around my archives, I came up with a CTF question that I prepared for Game of Pwners CTF 2017.
This was a preliminary question as far as I remember.
Here is the ctftime URL: https://ctftime.org/event/406
I’d like to write down whatever I remember and all of the docs that I found.
The question:
He doesn't have an username on Telegram! We need his Caller-ID.
received_signal.zip
files in the zip file:
1) param.txt:
Bit_Period=.000001;
Amplitude=5;
F1=(1/Bit_Period)*8;
F0=(1/Bit_Period)*2;
Fs=99000000;
T=Bit_Period/99:Bit_Period/99:Bit_Period;
2) signal.dat:
4.9597741e+00 4.8397435e+00 4.6418397e+00 ....TRIM...
Hints
- www.ti.com/lit/an/spra462
- md Salim Raza
- www.w3schools.com/xml/xml_syntax.asp
As some of them are broken let me drop some screenshots below:
Answer
1) Open/import .dat file into Matlab.
2) FSK-Demodulate the signal by using parameters. (FSK is used to be using for CallerID). Output is in binary: 0110001001101001011101000010111001101100011110010010111100110010011010110011000101100010011100010110110101010010
You can use the following code in order to demodulate, it belongs to md Salim Raza (Remember hints) https://de.mathworks.com/matlabcentral/fileexchange/44821-matlab-code-for-fsk-modulation-and-demodulation After a registration it’s possible to download the matlab code.
3) Convert binary to ascii then obtain URL below: bit.ly/2k1bqmR It redirects to canyoupwn.me/we_eavesdropped_his_phone/
4) There is an XML file under this URL. You need to open it with wireshark but errors pop-up because of the syntax issues as shown below:
<?xml version="1.0"?>
<dump>
<l1 direction="up" logicalchannel="128" error="0">
<l2 type="I" txseq="0"rxseq="1" p="0" data="03450404600200815E06813XXXXXXXXXA1150103" >
<!--
Caller is from turkey(+90), you need to get in touch.
Tell him: "Can you hear me now?"
-->
After fixing XML tags, you should be able to open. Remember the 3rd Hint above… Note: I replaced with XXX.. to be avoid of leaking his phone number.
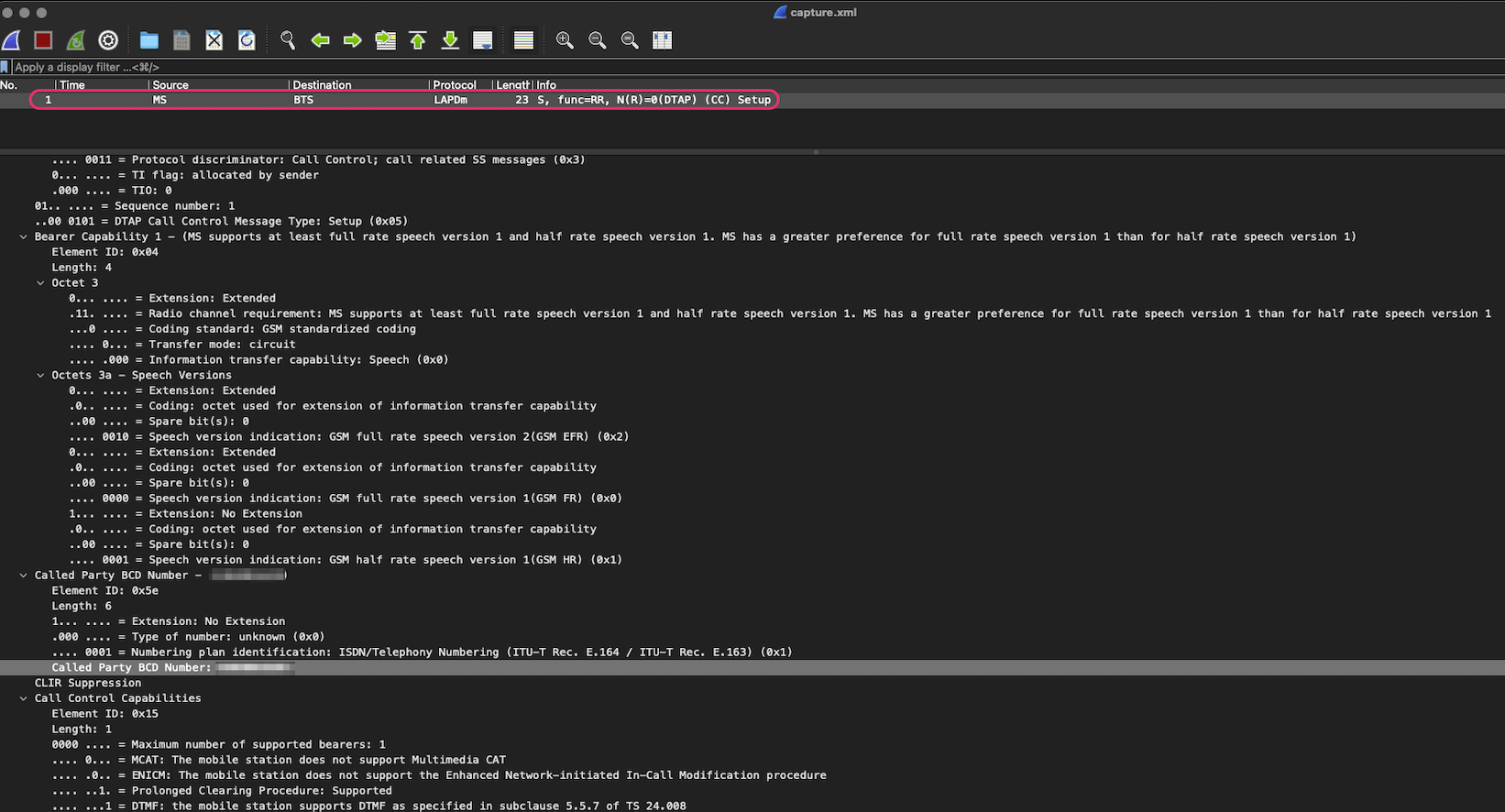
5) When you open the XML with Wireshark then you should be able to see a GSM capture. When you open it, you should be able to see Caller-ID.
6) Caner Koroglu was supposed to be replying back the flag to you on Telegram :)